New Stealthy Linux Malware Targeting Endpoints & IoT Devices
- This author does not have any more posts.

At AT&T Alien Labs researchers have discovered a new stealthy Linux malware called Shikitega that can infect Linux systems in a stealthy manner. With additional payloads, the primary target of this Linux malware is the Linux-based systems and IoT devices.
In addition to exploiting vulnerabilities, the malware adds persistence to the host through crontab by exploiting exploits to elevate privileges. Later a cryptocurrency miner is installed on an infected device as a result of the infection.
It is quite easy for Shikitega to escape detection by anti-virus software since it is a stealthy malware. This malware uses a polymorphic encoder to evade detection, which means that it is impossible for any static, signature-based analysis to be performed on it.
Infection chain
This malware is spread through the use of a very small file called ELF that acts as a main or primary dropper. In total, the code takes up about 300 bytes while the total size is about 370 bytes, so the program is quite small.
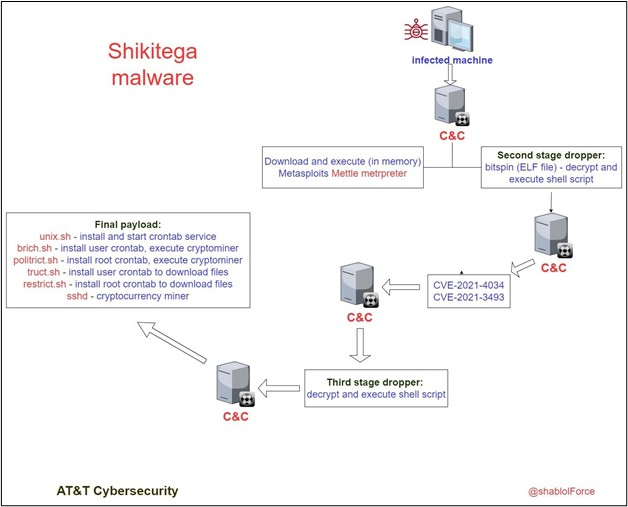
At this point, we don’t know the exact method by which the infection spread for the first time. There are multiple steps in the malware infection process in which each layer only delivers a few hundred bytes to the target.
In order to activate a module, one must activate a simple module, then move on to the next module. There is a shell code encoded in the ELF file, which is the dropper file.
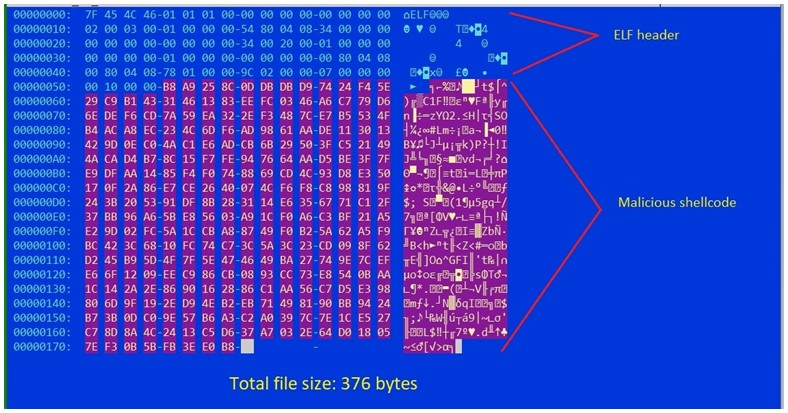
An additive feedback encoder called Shikata Ga Nai is used for the encoding process. In order to decode the data, the malware runs through several decoding loops using the encoder.
A dynamic substitution of instructions and a dynamic block ordering is used in order to generate the encoder stud. A dynamic selection of registers is also carried out in addition to this.
A shellcode is executed following the decryption to intercommunicate with C2 of the malware. After receiving the shellcode (commands), they are used for running from memory additional shell code.
A Metasploit Meterpreter payload known as “Mettle” is downloaded and executed via one of these commands. A host can then be remotely controlled and code executed by an attacker.
The Mettle program is configured to fetch a smaller ELF file, and it exploits the following vulnerabilities:-
- CVE-2021-4034 (aka PwnKit)
- CVE-2021-3493
As a result of these flaws, the following exploits have been carried out:-
- Elevate privileges
- The payload for the final stage is downloaded here
- Deploy a cryptocurrency miner as a root
Scripts Used
Here below we have mentioned all the scripts that are used to achieve persistence:-
- unix.sh: Check if “crontab” commands exist in the system, if not install it and start the crontab service.
- brict.sh: Adds crontab for the current user to execute crypto miner.
- politrict.sh: Adds root crontab to execute cryptominer.
- truct.sh: Adds crontab for current user to download cryptominer and config from C&C.
- restrict.sh: Adds root crontab to download crypto miner and config from C&C.
Recommendations
Here below we have mentioned all the recommendations recommended by the cybersecurity analysts:-
- Make sure that the software is updated with the latest security patches.
- Make sure all endpoints have anti-virus software installed as well as EDR software.
- To make sure that your server files are backed up, you should use a backup system.
- Make sure to have a robust security strategy
Resource : https://cybersecuritynews.com/new-stealthy-linux-malware-targeting-endpoints-iot-devices/