How Windows 11’s Enhanced Phishing Protection guards your password

One of the easier ways to steal a user’s credentials is through a convincing fake login page or application. An unwitting user can quickly give an attacker the crucial “in” to an organization’s systems with the everyday act of entering their password in the wrong place.
Often a phishing attempt shows up in the form of an email that looks dangerously close to the real thing and directs a user to a fake login page. The truly convincing phishing attempts mimic the logos, verbiage, and layout down to the pixel.
Often, the only giveaway is the URL, but there are ways to obfuscate and hide this as well.
Protecting Users with Enhanced Phishing Protection in Windows 11
To help combat the constant risk of password theft, Microsoft added phishing protection in Windows 11 Version 22H2.
When enabled, Enhanced Phishing Protection is offered through Microsoft Defender SmartScreen. But what does this actually offer for users?
Enhanced Phishing Protection inspects the URLs and any running processes to evaluate whether the site or application appears to possibly host malicious content or is insecure.
If so, SmartScreen leverages telemetry data from a multitude of Microsoft security products to notify the user and block the offending site or application.
As this integration is deeply integrated into Windows through operating system-level integration with Microsoft Defender, a deeper inspection of processes and URLs is available than many competing products offer. In addition, Enhanced Phishing Protection is offered as a baked-into Windows 11 capability without needing an additional install or license.
If Enhanced Phishing Protection detects a user entered their Windows password into a website or an application, an alert and prompt are shown warning the user to change their password.
If the password is simply entered into an application like notepad, the protection recommends that the user delete their password from that file.
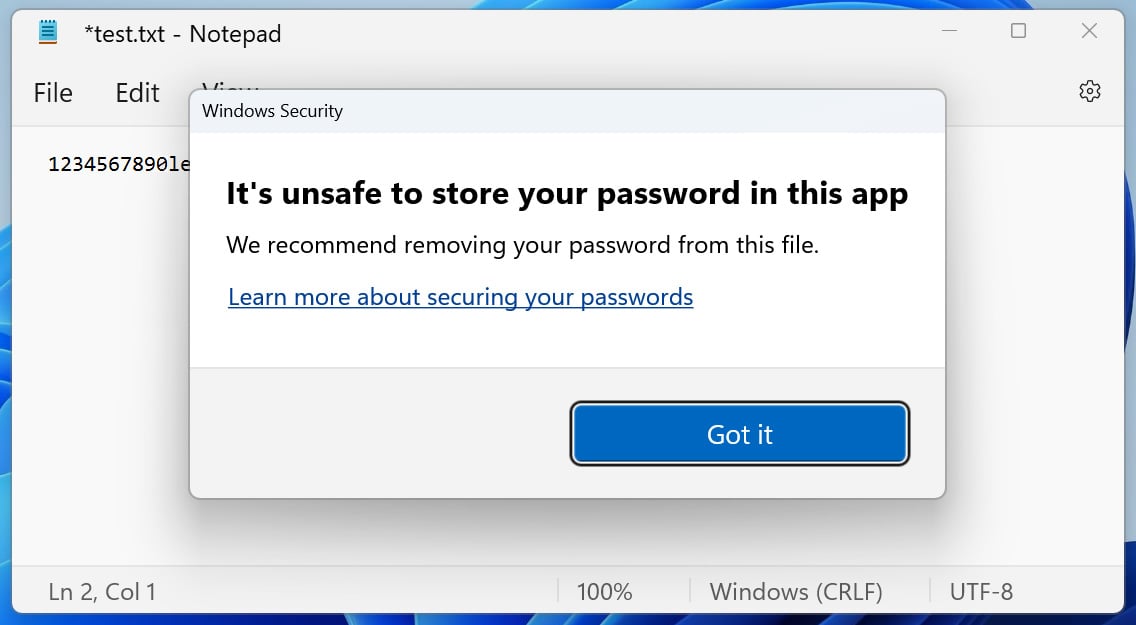
This proactive approach helps keep users safe and doesn’t allow a potential attacker to take advantage of their newfound credentials.
Real-World Consequences of Phishing Attacks
Phishing campaigns are becoming all too easy for threat actors to create.
A Phishing-as-a-Service (PhaaS) platform named Caffeine offers open registration and focuses on Microsoft 365 logins but with a subscription model and anti-detection and anti-analysis protections.
The speed at which a new threat actor can attempt a realistic phishing attempt on a victim is becoming difficult to contend with.
A real-world example of this is American Airlines. They found that an employee’s Microsoft 365 account was hacked. From this vantage point, multiple employee accounts were accessed and leveraged to send even more phishing emails from within the organization.
In filings, the data breach appeared to affect over 1,700 employees and customers. American Airlines now has to offer compensation and protection against future threats. Not to mention the time investment it will take to secure and handle the damage done by the phishing attack.
What to Consider While Configuring Enhanced Phishing Protection
As with most solutions, there are several caveats. This integration only works with non-Windows Hello logins. If you do not use a password to sign into your computer, then the Enhanced Protection is unavailable.
In addition, the browser-level integration only works with Chromium-based browsers at this time, which leaves Firefox out of the equation and Opera. As Microsoft Edge is Chromium-based, this makes sense for Microsoft but may not fit every organization’s requirements.
For system administrators, the Enhanced Phishing Protection is configurable via Group Policy which makes organization-wide rollouts easier.
These include settings such as whether to enable the feature, whether or not to notify a user of a malicious website, whether a password has been reused, or if an unsafe application has been detected.
For those using Microsoft Endpoint Manager, add Enhanced Phishing Protection to your users with a profile and the relevant settings. Adding to that, those organizations using Microsoft 365 Defender view alerts in the Defender for Endpoint portal.
The Other Side of the Coin: Specops Password Policy
Microsoft’s Enhanced Phishing Protection is only part of the equation; keeping track of passwords and blocking weak ones is the other side of actively protecting users and your organization.
With Specops Password Policy, you gain a constantly updated breached/stolen password list and powerful and customizable password policies.
Phishing attacks resulting in lost passwords make quick work of infiltrating an organization. But, an organization with Enhanced Phishing Protection paired with Specops Password Policy and Breached Password List functionality ensures that your users stay safe.
By scanning your accounts against a constantly updated list of over 3 billion+ breached passwords, when a stolen password is added to the list, you can take fast action and remove the potential vulnerability from your environment.
With the Specops Authentication Client, upon password changes, instantly inform your users as to why their password won’t work, even more so if the password has been stolen through a sophisticated phishing scam.
Specops Passwords offers much more than breached password protections; a slew of features exist to secure accounts and protect users from costly mistakes. Make sure that your users are using secure passwords by auditing existing accounts and providing invaluable feedback to make sure that your users know exactly what is expected.
A few of the valuable features Specops Password Policy has:
- Use custom dictionary lists to add words common to your organization.
- Block user names, display names, specific words, consecutive characters, incremental passwords, and the reuse of a part of the current password.
- Take advantage of granular GPO-driven targeting for any organizational unit (OU), computer, user, or group population.
- Use Regular Expressions to customize requirements further.
- Use helpful end-user client messaging at failed password changes.
Combine Microsoft’s Enhanced Phishing Protection and Specops Password Policy to protect both your users and your environment. You can test out Specops Password Policy in your Active Directory for free, here.
Resource : https://www.bleepingcomputer.com/news/microsoft/how-windows-11s-enhanced-phishing-protection-guards-your-password/

